Ethernity offers enhanced end-to-end networking security on FPGA through encryption and tunneling offload, avoiding server CPU involvement, achieving deterministic low-latency throughput with zero packet loss and reduced power consumption.
The Market Need
Today’s server-based network connectivity require security tools to protect data and users, especially from access to the aggregation points. Non-3GPP-compliant networks are being integrated into 5G architecture, Disaggregated network architectures are even more raising demand for crypto, IPSec, VPNs, and other security features. Adding security protocols to many other functions already running on server CPUs would add latency, power, and the potential for packet loss, so an offload solution is necessary.

Our Offering
Ethernity integrates a crypto engine into its ENET Flow Processors, thereby providing end-to-end routing and forwarding with IPSec termination without involving the server CPU in the VPN process. This offers a huge advantage in terms of data processing performance, as well as increased CPU protection, while reducing power requirements.
Ethernity’s FPGA-based networking security solution produces deterministic throughput together with IPSec at 10/25Gbps or more on our ACE-NIC SmartNICs, while promising zero data loss and latency of ~10 microseconds, which is significantly better than when running networking and security through a CPU.
Moreover, our Host Bypass feature isolates the traffic, packet editing, and encryption exclusively to the FPGA, entirely bypassing the CPU, which is vulnerable to breaches.
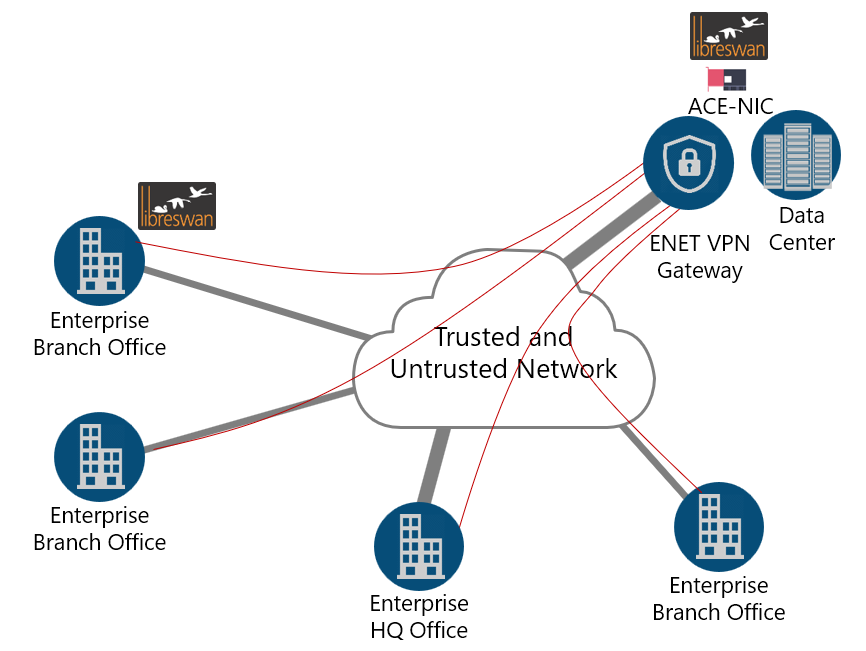
Ethernity offers its ENET VPN Gateway network appliance to enable the aggregation of multiple VPN tunnels and fully offloading networking security functions to the FPGA from the server CPU. Integrating widely-used open source Libreswan security management software into Ethernity’s fully programmable FPGA-based security appliance and accelerating it enables encrypted connectivity over untrusted networks. Most of all, the ENET VPN Gateway’s programmability ensures future readiness for integration of other existing open source software as well as new flow monitoring functions, security protocols, and crypto algorithms.
- Ideal VPN security solution for next-gen networks at the edge, in the cloud, or for enterprise data centers
- Offers complete programmability of control plane (handled in CPU) and data plane (handled in FPGA)
- Ideal for virtual environments with built-in slicing support
- Combines security and packet processing data plane in a single programmable low-power FPGA
- Easy to customize with new crypto protocols, overlay methods, or capturing capabilities
- Improves security by reducing opportunities to breach the CPU
- Uses open source Libreswan control stack
Network Security with the ENET VPN Gateway